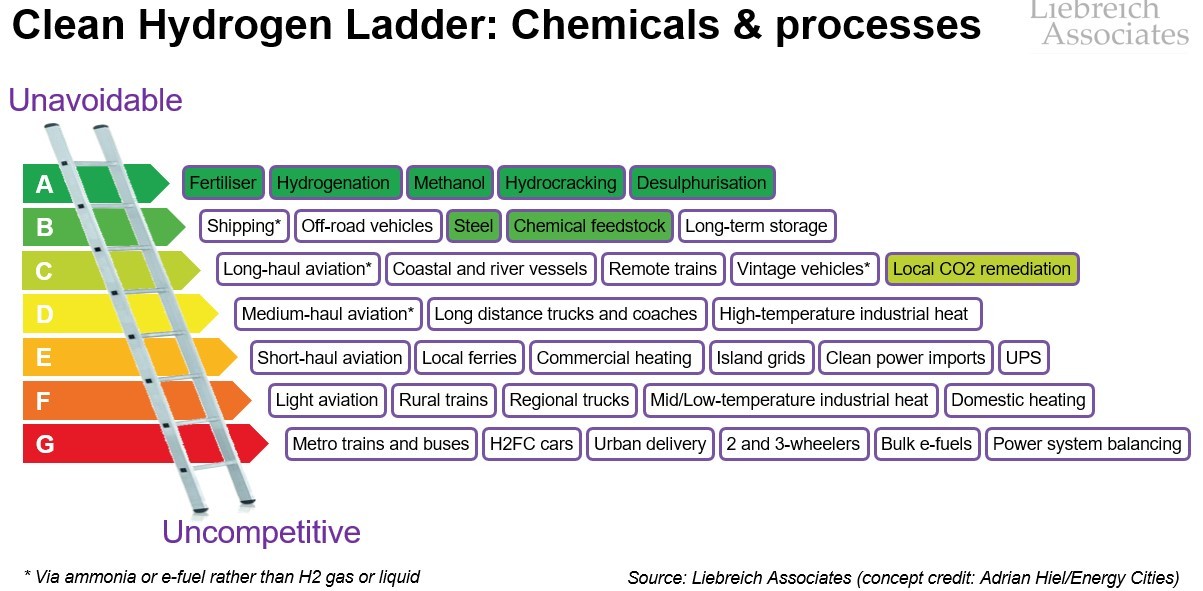
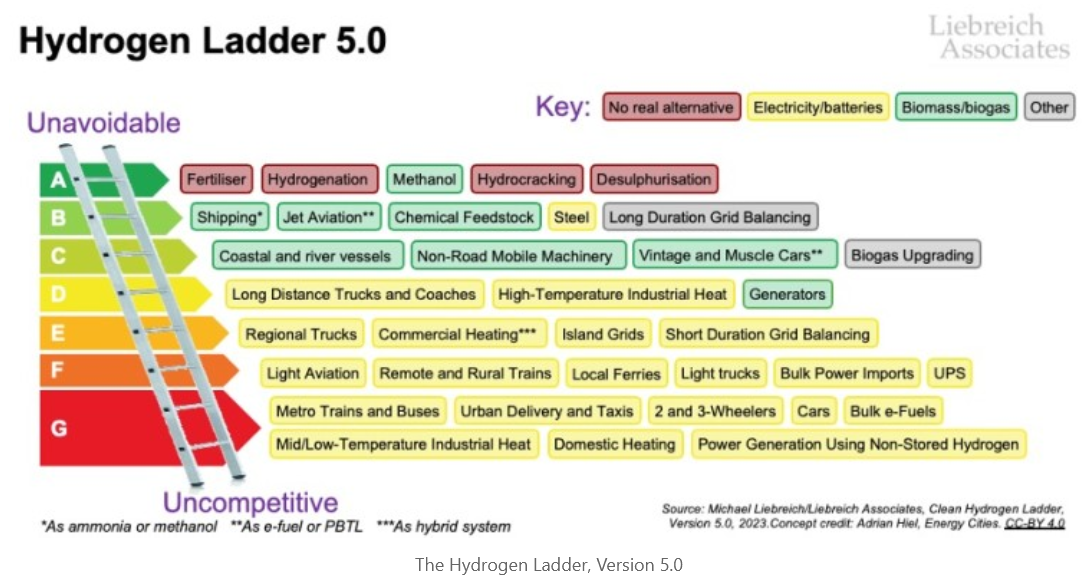
Prospect: ‘WannaCry’ the wake-up call we all needed – Time to get serious about cyber safety
Written for Prospect, click here to read the online article
The WannaCry ransomware attack, which hit the NHS hard and infected computers in over 150 countries, was a wake-up call. Our infrastructure is increasingly digital and connected—we need to get serious about protecting it.
The last few years have seen a number of large-scale, sophisticated cyber attacks. In 2011, 77m Sony PlayStation accounts were compromised. Since then hackers have penetrated MySpace (359m accounts stolen), LinkedIn (117m), eBay (145m), Target (70m), Experian (200m), Heartland Payment Systems (130m), Adobe (152m), Yahoo (1bn), the Philippine electoral system (55m)—the list seems endless.
Other attacks have been equally sophisticated but highly targeted, such as Stuxnet, originally designed to impede Iran’s nuclear programme, and last year’s raid on Bangladesh’s Central Bank, which came within a whisker of netting $1bn.
Until now, the consensus appeared to be that these attacks were an inevitable and irritating feature of modern life. Every so often a bunch of people have to change all their passwords and some hapless organisation takes a financial hit—but on a societal level that’s a small price to pay for the instant information and frictionless commerce we all now take for granted. The problem with this attitude is that as our economy becomes ever more digital and deeply connected, it is also becoming more fragile, to the point where the risk of a cascading collapse is very real.
In 2012, David Korowicz, physicist and human systems expert, modelled the implications of the ever-tighter linkages between our financial, energy and food systems. He found that a deep disruption lasting just a few weeks might be enough to make it impossible to “reboot” the earlier state of the economy, leading to the collapse of society. A sobering thought, given that it took weeks to restore power to all the homes affected by Hurricane Sandy in November 2012. Earlier this year, at least two people died from health emergencies during a blackout in Amsterdam that lasted only five hours.
The most recent Worldwide Threat Assessment of the US Intelligence Community, issued just before the WannaCry ransomware attack, sums up the nature of the cyber risk: “Nearly all information, communication networks and systems will be at risk for years… These threats are amplified by our ongoing delegation of decision-making, sensing and authentication roles to potentially vulnerable automated systems. This delegation increases the likely physical, economic, and psychological consequences of cyber attack and exploitation events when they do occur.”
The world’s energy system is in the process of transforming from a centralised, analogue, “dumb” system to one which is decentralised, digitally controlled and “smart”—saturated with sensors, software that makes local optimisation decisions, and communications connections. Our transport network is going the same way. While opinions differ on when we will see truly driverless cars roaming our cities, they are certainly coming; meanwhile, our transport system is already dependent on smartphones, digital maps, ride-hailing apps and communications software. In 1983, 11 out of 12 Americans aged 20 to 24 had a driving licence. By last year, one in four did not. In the first quarter of 2016, more cars were added to the US cellular network than phones.
The trend does not stop with energy and transport: our water and waste systems, agriculture, healthcare, manufacturing and chemicals industries, even our homes and offices, simply cease to function if they are denied access to electrical power, the internet and the payments system. And as these industries become more intimately linked, so the risks multiply. When hackers stole 70m consumer records from retailer Target in 2014, they gained access via an air-conditioning contractor’s system. Last year a significant number of websites, including Airbnb, Netflix and Twitter, were taken down by massive DDoS (Distributed Denial of Service) attack launched by a botnet called Mirai, which had taken advantage of millions of poorly set-up devices, such as webcams and thermostats.
It is not just cyber criminals who might be targeting our infrastructure, but state actors. In 2013 an Iranian hacker conducted an intrusion into the industrial control system of an American dam, and last year a Russian hacking operation dubbed Grizzly Steppe by the Obama administration was detected within the systems of a Vermont utility. Russian-based hackers have also been accused by Ukraine and the Baltic states of attempts to compromise their power and petrol distribution systems. Reports of cyber attacks originating in China have reduced since the 2015 US-Chinese Cyber Agreement, but in 2011 Chinese hackers attacked a number of US oil, gas and petrochemical companies.
It’s not only hacking, whether by criminal or state actors, which we should fear. For the past few years the tech world has been enchanted by the promise of services like IFTTT (If This Then That), which offers an easy way to control physical devices around the home. But during an outage at Amazon Web Services, the cloud-based services used by IFTTT and a huge number of other businesses, IFTTT users found they could no longer turn on their lights or air-conditioning. In South Australia, when a storm took out a major power line, the resulting voltage fluctuations caused a raft of wind farms to shut down; the system operator had failed to manage the increasing complexity of the system.
We have all had a lucky escape with WannaCry: an IT expert studying the malware inadvertently stopped it in its tracks by buying an unused domain mentioned in its code. We may not be so lucky next time. It really is time to heed the wake-up call, and invest appropriate time and resources in protecting this wonderful, efficient, rapidly-digitising world of ours. And that goes for all of us.
Terms of use: photos and other media may be used exclusively for the purpose of publicising an upcoming or past event involving Michael Liebreich, or to illustrate an article written by him. Their use must be accompanied by a clear indication of copyright in the following form:
© Liebreich Associates/name of photographer. Photos or other media downloaded in this way remain the property of Liebreich Associates Ltd. Any infringement of these terms of use may result in legal action by Liebreich Associates Ltd or by the respective photographer or rights holder.